in cve, sql-injection
CVE-2025-10878 | SQL Authentication Bypass in Fikir Odaları AdminPando
CVE-2025-10878
SQL Authentication Bypass in Fikir Odaları AdminPando
Summary
| Field | Value |
|---|---|
| CVE ID | CVE-2025-10878 |
| Product | Fikir Odaları AdminPando |
| Vendor | Omran İnşaat A.Ş. |
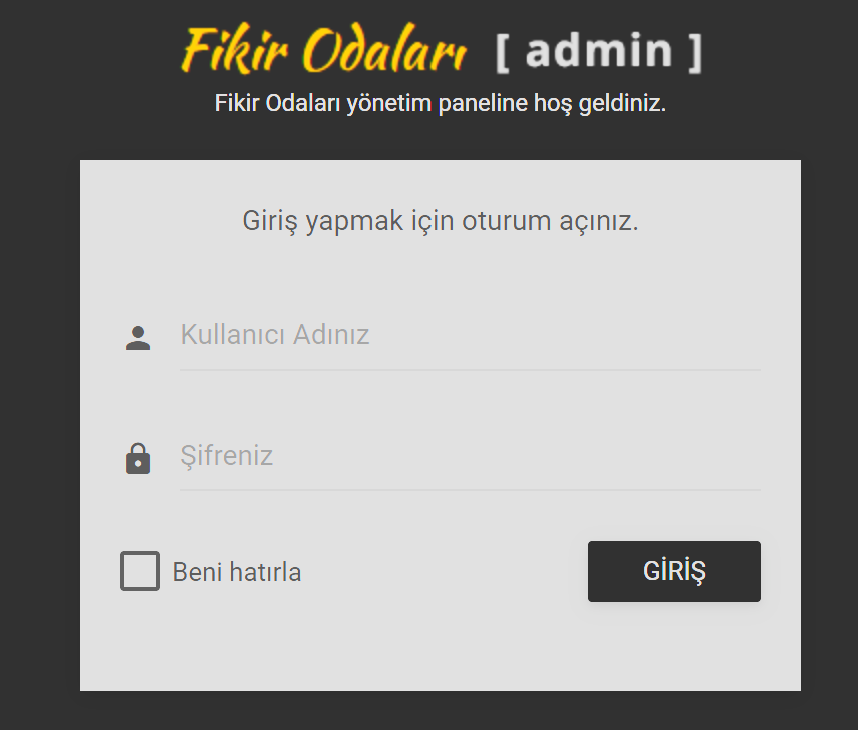
| Vulnerable URL | https://www.omran.com.tr/admin/logIn.php |
| Affected Version | v1.0.1 (and possibly earlier) |
| Vulnerability Type | CWE-89: SQL Injection |
| CVSS v3.1 Score | 10.0 (Critical) |
| CVSS Vector | AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H |
| Patch Date | 2026-01-26 |
| Researcher | Onurcan Genç |
Description
A SQL injection vulnerability exists in the login functionality of Fikir Odaları AdminPando v1.0.1. The username and password parameters are vulnerable to SQL injection, allowing unauthenticated attackers to bypass authentication completely.